


DS: What made you start PIA in the first place? Did you have a particular population or use case—or set of use cases—in mind?
AL: Primarily PIA was rooted in my humble beginnings on IRC where it had quickly become important to protect one's IP from exposure using an IRC bouncer. However, due to jumping around in various industries thereafter, I learned a lot and came to an understanding that it was time for privacy to go mainstream, not in the "hide yourself" type of sense, but simply in the "don't watch me" sense.
DS: Had you wanted to open-source the code base all along? If not, why now?
AL: We always wanted to open-source the code base, and we finally got around to it. It's late, but late is better than never. We were incredibly busy, and we didn't prioritize it enough, but by analyzing our philosophies deeply, we've been able to re-prioritize things internally. Along with open-sourcing our software, there are a lot of great things to come.
DS: People always wonder if open-sourcing a code base affects a business model. Our readers have long known that it doesn't, and that open-sourcing in fact opens more possibilities than leaving code closed. But it would be good to hear your position on the topic, since I'm sure you've thought about it.
AL: Since Private Internet Access is a service, having open-source code does not affect the business' ability to generate revenue as a company aiming for sustainable activism. Instead, I do believe we're going to end up with better and stronger software as an outcome.
DS: Speaking of activism, back in March, you made a very strong statement, directly to President Trump and Congress, with a two-page ad in The New York Times, urging them to kill off SESTA-FOSTA. I'm curious to know if we'll be seeing more of that and to hear what the response was at the time.
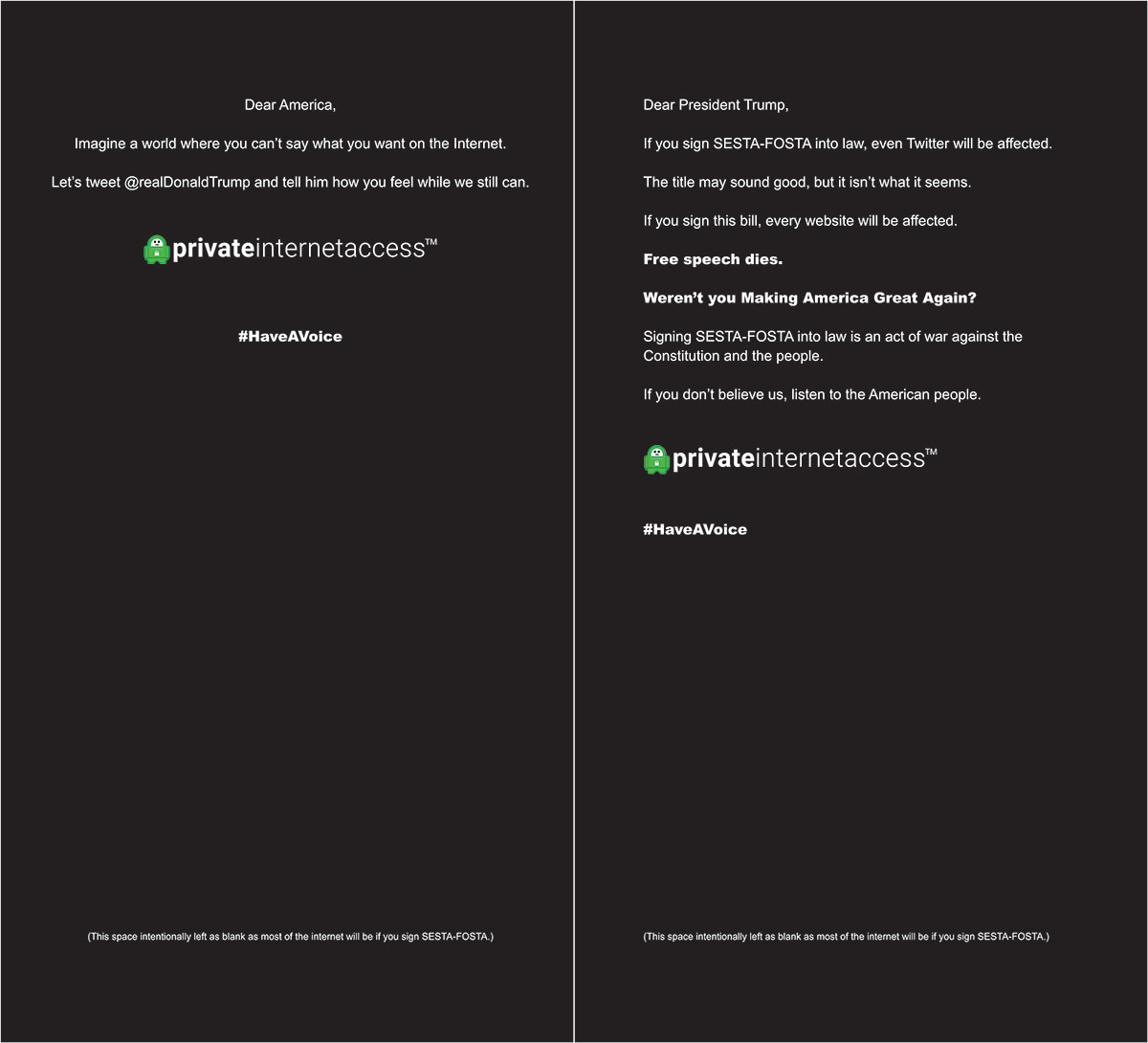
AL: Absolutely! We ran a few newspaper campaigns, including one for the Internet Defense League. It's a very strong place to mobilize people for important issues for society. As a result of the campaign, many tweets from concerned Americans were received by President Trump. I would say it was a success, but from here it's up to our President. Let's hope he does the right thing and vetoes it. That said, if the bill is signed in its current form [which it was after this interview was conducted], the internet is routing, and the cypherpunks have the power of the crypto. We will decentralize and route around bad policy.
DS: Our readers have always cared a lot about licenses, so here's a question for them: why the MIT license?
AL: Our internal open-source task force was given the mission of choosing the least restrictive open-source license possible, and they landed on MIT. I hope that anyone and everyone can benefit from our code however they see fit.
DS: Why release code repositories gradually instead of all at once? What kind of work do you need to do to make the code ready?
AL: In order to release our code properly, we're making sure we're distributing everything properly and with clean, readable code.
DS: Is the code on GitHub?
AL: Yes, at https://pia-foss.github.io.
DS: Tell us more about the VPN industry. How has it changed since you started PIA? And do you expect that open-sourcing PIA's code will help the company lead the market in new ways?
AL: I think a lot more companies have entered the VPN industry. For us, open-sourcing our code is part of a multi-part strategy to create what we call the "next VPN". We're not intending to lead the market, but instead to create a new market that will essentially put the existing market, in its current form, into extinction immediately. This strategy includes a heap of technology stacks we are building internally as well as simple feature additions. While we've definitely earned the reputation as the most-trusted VPN in the space, the primary goal of the our "next VPN" project is to remove trust from the equation. After all, we're strong believers in the words "in crypto we trust".
DS: I know PIA always has been adamant about not logging its customers. In 2015, the company had a chance to show why when a court subpoenaed customer usage records—and it was unable to provide any. I'd like to hear more about your philosophy there.
AL: Simply put, everyone has a right to privacy, but there are also choices. That's why I think it is imperative for people in the VPN consumer market to do research beyond simple reviews. Instead, find forums and look for dirt on companies. That's the best way to verify any company—in our space or any others. Do searches that fill in the blanks on who sucks, who monitors their users, who logs their users and so on.
DS: Make the connection, if you don't mind, between open source and privacy.
AL: For us, open-sourcing is vital given that, in order to protect one's privacy, it is important for people to know exactly what it is their software is doing. Having the source code available makes this possible. I also believe that it further enhances security, in addition to our third-party audits that we already performed, since more eyes will be able to review the code.
DS: What's next?
AL: With PIA we're really building the "next VPN", and it will be more private than the way current providers look, on an order of magnitude. However, I really don't want to talk about it. We prefer to deliver, rather than talking about what we'll deliver.
DS: Today we're seeing the pendulum swinging toward decentralization, and greater individual autonomy and control. I'd love to hear about how you see that playing out, in what sequence and with what likely populations.
AL: Everyone has a different threat model, and everyone needs clear choices about trade-offs. To start, we're providing Tor to provide people with one of the most essential choices. I don't like talking about stuff in the pipeline, but I will say we're launching full Tor support in all of our clients on desktop and mobile. This is going to allow our end users to route through Tor, which effectively allows them to mask their identity further. I believe that this will be used by a smaller set of users than our overall customer base, because the Tor network is still small. However, by educating people about Tor while the network grows, so will Tor's efficiency.
DS: I assume crypto will be involved. Can you say more about how?
AL: Everything we do uses crypto, from the algorithms used to even some of the accepted payment methods, such as cryptocurrencies. In launching our "next VPN" solution, we are relying heavily on cryptography and the unique applications to which it can be applied. It's pretty crazy that nature, and brilliant people, have given us a gift, weapon and protection in the form of cryptography, and we're damn sure going to be betting everything we've got on it.
DS: How do you see VPN usage, and the whole VPN market, evolving and changing, especially in different settings?
AL: I believe the VPN market and usage will continue to increase, as it already has, given the political and social climate. Many countries and companies are totally abusing their citizens and users, and people are learning that they need to take matters into their own hands to protect themselves.
DS: With all the bad news around Facebook and the approach of the GDPR and other privacy regulations, what changes do you see coming, from your perspective as a provider of privacy tech?
AL: I'm guessing privacy will continue to be an important value to people. That being said, the government is constantly in a never-ending battle to remove our privacy. This is pretty bad, because privacy is more than just our right to disclose information to whomever we want, when we want; it's actually a tool that allows us to be unique. Without privacy, we will all become conformists and do whatever it is "the man" deems appropriate. Screw that world. Seriously. We have to blend into the crowd and become anonymous, believe it or not, in order to become different and characteristically unique. But this fight won't be easy. It's a fight for control.
DS: So you see a conflict coming—or already here and headed into some showdowns?
AL: Yes. My perspective is that the Crypto War is heading to the main event. We'll all need to work together to fight for the sake of cryptography and, even more broadly, the internet.