

How to safeguard your personal data with TrueCrypt and SpiderOak.
There are so many cases of personal identifiable information (PII) or any type of data exposed on the Internet today. The details provided in this article may assist in safeguarding your tax information, social security number or password file. The setup this article describes will help keep your personal data at home safe and secure in this “cyber-security”-connected world. This includes virtual/physical security compromises—the only truly secure system is one that is unplugged and locked in a vault. This solution is not all-encompassing and does have limitations, but it is sound enough for safeguarding personal data.
The first step is addressing the physical aspect of security. This is a critical step, because some notable compromises are a direct result of someone having physical access to a system. You always should prepare yourself for the possibility that your beloved electronic devices could be in hands of someone other than you at any given moment. This situation could occur on a train, or in a coffee shop, automobile or home, and you must assume your data is lost when it is outside your control.
This article describes utilizing whole disk encryption to reduce some of the risks provided by a great open-source Linux operation system (Ubuntu 12.10). Whole disk encryption is a key factor, especially when considering all of the recent events concerning stolen government laptops that contained millions of social security numbers.
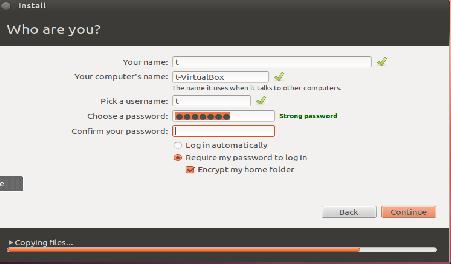
Figure 1. Setup screen for encrypting your home directory in Ubuntu during initial operating system installation.
The next key step in safeguarding your personal information is by adding another security layer by encrypting home directories during the initial installation (Figure 1). You may be the only one using this system; however, if others are able to access your system while it's running, this may slow them down from trying to access information contained in a home directory.
You will need to run the command:
sudo apt-get install ecryptfs-utils cryptsetup
using an advanced packaging tool-capable distribution. This will install the encrypting utilities needed to encrypt your home directory.
The next step is to log in or create another user account with root privileges to run the following command on the user's home directory (Figure 2):
sudo ecryptfs-migrate-home -u your-user-name
Then, you need to log in to the encrypted home directory account before rebooting the machine (as stated in the important note screen), providing a roll-back opportunity in the event of any unexpected complications during the encryption process.
Use encryptfs-unwrap-passphrase to record your randomly generated mount passphrase. Keep this passphrase safe, because you may need it to recover your encrypted files. Also, ensure that you reboot your system and remove the un-encrypted backup folder (Figure 3).

Figure 2. If encrypting your home folder was missed during initial installation, use encryptft-utils to encrypt your home directory.

Figure 3. This is important feedback information “record passphrase as soon as possible” that will be generated from the encryptfs-migrate-home command.
A third step in the process is to utilize a great open-source application called TrueCrypt to provide encrypted containers to store personal information. This easy process includes visiting the TrueCrypt Web site at www.truecrypt.org/downloads to download the latest package (truecrypt-7.1a-linux-x86.tar.gz, at the time of this writing), and run the following commands and script:
tar -xvf truecrypt-7.1a-linux-x86.tar.gz sudo ./truecrypt-7.1a-linux-x86 select ? Install TrueCrypt at the gui menu.
Figure 4. TrueCrypt Installation Button
The next step is to create an encrypted container. This container will store personal identifiable information (PII) or any file that you want to keep safe on your local computer, and it will create another layer of security. The process for creating a basic container is by selecting the default options during initial installation (Figure 4). Once the software is installed, starting the application is a breeze using the command truecrypt & or via the GUI menu system by selecting the create volume button.

Figure 6. After the create volume button is selected, you will be presented with two options for creating an encrypted file container or creating a volume within a partition/drive.
There are two options when creating a volume: choosing an encrypted file container or a volume within a partition/drive (Figures 5 and 6). You also will have a choice of using a standard TrueCrypt volume or a hidden TrueCrypt volume (Figure 7). The idea behind a hidden container is to reveal an outside container password, and your hidden container encrypted within the outside container (www.truecrypt.org/docs/hidden-volume).
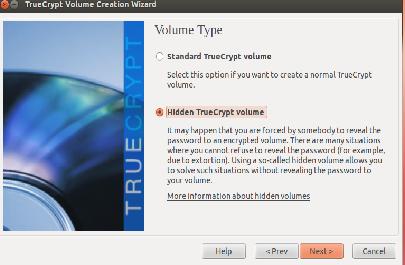
Figure 7. The next menu item gives you the option of creating a standard or hidden volume.
On the next menu, simply select an encryption algorithm, hash algorithm and size of container. Multiple books and papers provide specific information on the differences between these algorithms and hashes (AES with a 256/14 rounds and Sha-512 default hashing function). The size of your container depends on the amount of information you want to protect (Figure 8).

Figure 8. After the standard volume is selected, the next options are to select the encryption and hash algorithms, and size of the volume.
The next step is to select your preferred filesystem type (ext3, ext4 and so on). Once the volume-creating process is completed, mount your volume using the TrueCrypt application and start saving your private files to this encrypted container.

Figure 9. Select the newly created standard volume to mount an accessible unencrypted share.
A safe and secure on-line storage location for your newly created encrypted container is essential for backing up data in the cloud. A couple options are available for an on-line storage location, such as Dropbox, Evernote, AWS and SpiderOak. The final choice for secure cloud storage is with the company called SpiderOak, and this is based on the company's “Zero-Knowledge” privacy policy that states: “we never have any knowledge of your password and no way to retrieve or reset it, even in emergencies. It's our way of ensuring that our customer's data is always completely secure—even from us!” (https://spideroak.com/faq/category/privacy_passwords).
The company also provides two-factor authentication for extra protection of requiring a user name, password and a token. The token will be sent to your mobile phone whenever you need to log in to a Web site or mobile device. The majority of big-name providers are offering two-factor authentication since the traditional password/passphrase does not offer enough protection. Seeing how this solution is deployed on a dedicated desktop and requires the token to authenticate, it provides a true two-channel authentication solution. Of course, using two-factor authentication does not guarantee safety, but it does require the attacker to use sophisticated methods, and attackers generally are lazy and look for easy targets.
Installing SpiderOak is straightforward for all the Debian users out there. It includes downloading and installing the spideroak_4.8.4_i386.deb package from https://spideroak.com/opendownload and using sudo dpkg -i spideroak_4.8.4_i386.deb to install this package on your favorite Ubuntu platform.
Identify a local upload folder as the staging point for your TrueCrypt container. Once you have a shared location that will host your TrueCrypt container, simply open your SpiderOak application and select the backup tab. Then, drill down until you find your TrueCrypt container location, such as home/username/SpiderO/Upload.
The next step is to configure your backup frequency using the overview tab and selecting the change button (Figures 10 and 11).

Figure 11. A SpiderOak application status and backup menu provides a means to back up your encrypted volume automatically in specified intervals.
Many other configuration options are available using this interface. For this example, use only these two options for a secure cloud backup.
The last couple steps in this encrypted backup solution are to move the TrueCrypt container from the working location to the designated SpiderOak export folder and create a cron job to run the script.
I created a Python script to accomplish the copy function, but I could have created any type of script. This script is used to ensure that the TrueCrypt application is not running, verify whether there were changes to the container and then copy over the container if there were changes. This script requires a configuration file called FolderandFileLoc to function and the Python script BackupScript.py. The configuration file parameters are SpiderOakPath, TrueCryptPath and LogFilepath, a running log to verify whether a copy was successful and the Safefile filename.
The final step is to create a cron job to call the Python script:
0 5 * * * cd /home/t/workspace/BackupScript/src; /usr/bin/python /home/t/workspace/BackupScript/src/BackupScript.py
This personal encrypted solution is something that works great at home when utilized on a daily basis. Many apps are available on the Internet for managing passwords and data, but this one is easy to implement and provides layers of encryption. I am confident that using the described encrypted containers and storage location provides enough security for private personal data, but it may not be an ideal solution for an enterprise with various regulatory agencies. Use the described methods at your own risk, and ensure that your passwords or passphrases are safeguarded, because your data will be lost with a forgotten password.