

Your phone can do much more than make calls and install apps that make obnoxious noises—learn how you can use it to lock your screen automatically.
If you've ever worked with pranksters, you've probably come across this classic office prank. First, the unsuspecting victim leaves his computer and goes to lunch or a long meeting and doesn't lock his screen. The prankster then takes a screenshot of his current desktop, hides all the desktop icons and any taskbars, and sets the background to be the screenshot the prankster just took. When the victim gets back to his computer, none of the icons work, and no programs will open, yet when he inevitably reboots, even that doesn't fix it. Around the time he calls the desktop support team, the prank is revealed and everyone has a good laugh about it—except maybe the victim, who vows from that day on always to lock his screen.
I don't know about you, but even though I've never been the victim of a prank like that, I've always tried to be good about locking my screen when I'm away. I imagine some of this just stems from trying to be thoughtful about security, but also, if you are a sysadmin, you often have access to a lot of sensitive systems and data. Although you'd like to extend trust to your coworkers, an unlocked sysadmin computer would be a great source for sensitive information if you were a disgruntled employee. In this article, I discuss a simple program I've found that works great to lock your screen automatically when you walk away. At the end of the article, I also discuss some ideas for how to hack in to a system protected by this software.
Traditionally on any desktop environment I've used, I would configure a Ctrl-Alt L keybinding that locked my screen. It was so committed to muscle memory, that the moment I was about to stand up, my fingers automatically would lock my desktop without thinking about it. Although this method works great, I've recently discovered just how easy it is to set up your desktop to lock automatically when you leave, and even better, to unlock automatically when you return.
The solution to proximity-based desktop locking has been around for a while. I remember Linux Journal's own Bill Childers demonstrating such a thing to me with Bluetooth on a Mac more than six years ago, but I've never felt like messing around with the Bluez tools on Linux to write my own script. It turns out these days there's a simple program you can use to lock your screen via Bluetooth that takes only a minute to set up: BlueProximity.
Essentially, BlueProximity works on the notion that most of us carry around a Bluetooth device with us—our cell phone. Because Bluetooth works only over a limited range, with a bit of tuning, you can make some assumptions about how close a device is to your computer based on the strength of its signal. BlueProximity works via these assumptions to decide when to lock or unlock your screen. When you leave your computer, the Bluetooth signal gets weaker until it crosses a threshold, and your desktop is locked. When you return to your computer, the signal gets stronger until it crosses a different threshold, and the computer automatically unlocks.
You install BlueProximity much like any other Linux program: with your package manager. In my case, the package simply was called blueproximity. Alternatively, if your distribution doesn't package it, you can download and build the software from the source available at the BlueProximity SourceForge page. Once installed, you either can type blueproximity in a terminal to launch the program or click on it in your applications menu (on my system, it showed up under the Accessories category).
Once you start the program, you will get a new icon in your panel and also see a window much like the one shown in Figure 1. BlueProximity requires that the device you set up already has been paired with your computer, so if you haven't yet paired your phone (or other Bluetooth device you wish to use), you need to go through the steps to pair your Bluetooth device first. In my case (on an Ubuntu system), I first made sure Bluetooth was enabled and visible on my phone, next I clicked System→Preferences→Bluetooth, then clicked Set up new device, and after that I just followed through the wizard that appeared.
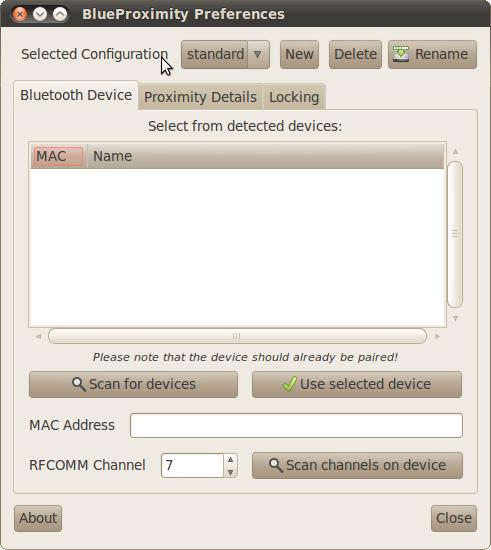
Figure 1. The Default BlueProximity Tab
After you pair the Bluetooth device, go back to the main BlueProximity screen and click on Scan for devices. It may take a bit for the scan to complete, but afterward, you should see your Bluetooth device on the list. At that point, just select it, click Use selected device, and your device will be configured and ready to use. You can safely click the close button at the bottom of the window, as BlueProximity will still stay in your panel.
Out of the box, BlueProximity tries to use reasonable settings to determine when to lock your screen; however, each Bluetooth device is different, and I've personally seen that different Bluetooth devices can have much different antenna strengths. If you notice that your screen doesn't lock as soon as you'd like, or worse, if it locks while you are still at your desk, click on the Proximity Details tab where you can edit thresholds (Figure 2). In this window, you will find a number of different sliders. The Distance slider for both Locking and Unlocking lets you control how close you need to be to the computer. The Measured atm slider updates every second or so and shows the current distance BlueProximity reads, so you can get a sense of how sensitive your equipment is. The Duration sliders let you control how long the device needs to be at a certain distance before it locks or unlocks the screen. This is useful in particular when tuning the Locking section so that one bad reading doesn't lock your screen when you don't want it to.
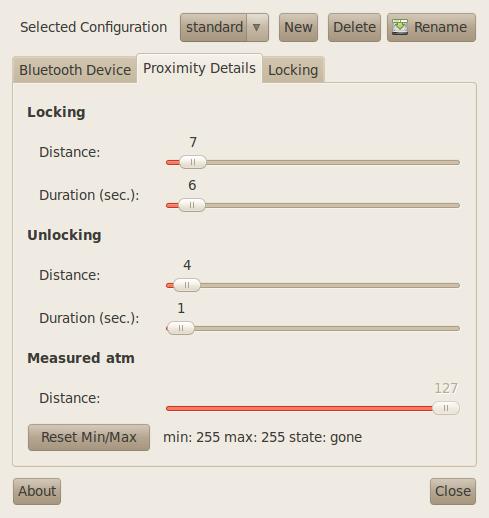
Figure 2. The Proximity Details Tab
If you do notice that the screen locks on you often while you are at your desk, increase the Distance slider for locking. Alternatively, if you notice when you come back to your desk you have to sit there for some time before it unlocks, you may want to increase the Distance slider for Unlocking and decrease the Duration slider if it's higher than one. Just make sure that your unlocking distance isn't higher than your locking distance.
By default, BlueProximity is configured to trigger gnome-screensaver commands. If you use GNOME, that might be fine, but if you use another desktop environment, click the Locking tab (Figure 3) where you can change what command gets run to lock and unlock the screen. By default, you can choose between gnome-screensaver and xscreensaver from the drop-down list, but you could really put any script you want in here. For instance, you might want to create a locking bash script that not only calls gnome-screensaver but also uses a DBUS signal to pause your music. Then you could write a similar script to unpause your music and unlock the screen when you return.
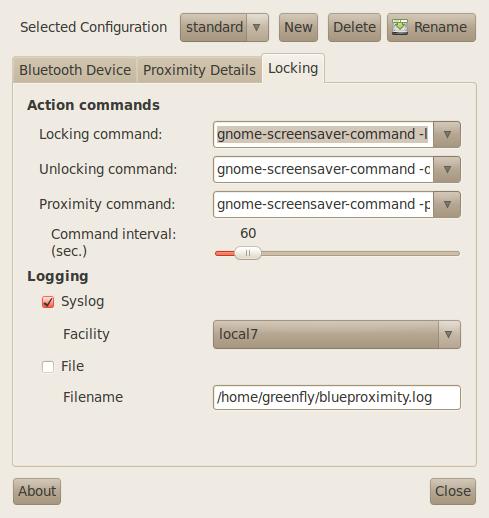
Figure 3. The Locking Tab
Security is often a trade-off for convenience. BlueProximity is interesting in that it tries to increase your security (by automatically locking your screen), and it also tries to increase your convenience (by automatically unlocking your screen when you return). It is this convenience that may possibly open you up to an attack. That said, BlueProximity and the Bluetooth protocol do make attacking this method rather difficult, because BlueProximity allows only one device to unlock it at a time. You may think you could hack this setup simply by cloning the MAC address of a person's phone on your Bluetooth device. Although this is possible, unfortunately, during the pairing process, keys are shared between the two devices that they will use for secure communication later on, so even if you can clone a phone's MAC address, it still will not necessarily accept your device, because you don't have the shared secret. That having been said, Andrew Y. Lindell released a paper for Blackhat 2008 demonstrating that if you could sniff the pairing procedure, the password potentially could be leaked to you. Even if you weren't there when the devices were paired, the paper demonstrated how you might be able to get a device to re-run the pairing procedure.
Of course, such an attack is quite sophisticated and might be difficult to pull off. An easier approach simply would be to borrow the person's phone to make a phone call or check out an app when he isn't at his desk and then sneak over there. Along with that attack, BlueProximity naturally would be vulnerable to knocking the person out and stealing the phone, but then we are talking about office security here, and if you have to worry about coworkers beating you over the head and robbing you, maybe you should look into another line of work.