

One of the oldest games on your system has a convoluted history, deep, complicated dungeons and some spiffy new graphical front ends.
François, although I am very impressed with your initiative in documenting your experience in network security, that document will need some changes. Of course, I have not read it yet, mon ami, but I still know it needs some changes. Well, the title, for starters—somehow, I don't think you can call it “The Guide to Net Hack”. NetHack is a game, François, and it has nothing to do with network security. Well, not much, anyhow.
Quoi? You have never heard of NetHack? Mon Dieu, mon ami! This is something we must resolve immediately, if not sooner. Unfortunately, it is time to open the restaurant and our guests will be here momentarily, but perhaps...ah, too late, they are already here! Welcome, everyone, to Chez Marcel, home of the finest in Linux fare and, of course, the most extensive wine cellar in the Linux world. Please sit and make yourselves comfortable. François will fetch your wine immédiatement. François, please head down to the wine cellar and bring back the 1999 Catena Alta Cabernet Sauvignon from Argentina.
Just before you walked in, François made a rather humorous mistake, telling me he was writing a network security guide about Net Hack, not realizing that NetHack is a game. For those of you who may not know, NetHack is one of the most popular dungeon-crawling games of all time, and it has been around seemingly forever. Back when I first started playing NetHack, it was just called Hack (and before that, there was a game called Rogue). If you want the juicy details, a nice, concise history of the game is available from inside the game itself (press the question mark during game play). Over time, the game was transformed by a huge number of people scattered from one side of the planet to the other. The code also was ported to many different platforms and operating systems so you could play Hack or NetHack on just about any machine imaginable. Hack is gone, but NetHack lives and breathes to this day. This is a game that has captured the imaginations of scores of Netizens and continues to be a hugely popular game. Amazingly, NetHack in its pure form is a text-only adventure game (Figure 1), and it still often is played that way.
In text mode, and with scores of beautiful graphical games to pull from, NetHack may look too boring to keep anyone interested, and yet it still does. After all, your character is an @, your dog companion a d, a gold piece is a $ and so on. So why is a game like NetHack still so popular? It is because of the incredible richness and complexity of the game. The idea seems simple enough, but this is not an easy game and certainly not one you are likely to win in short order. Deep in the underground levels of the Mazes of Menace (or the Dungeons of Doom) lies the fabled Amulet of Yendor. To the one who finds the amulet, untold riches await along with the gift of immortality bestowed by the Gods. To gain the amulet, you must travel through the dungeons and mazes, encountering puzzles, strange objects, hidden pits from which there is no escape, demons, goblins, grid bugs and other monsters, including the simplest of dangers, hunger and thirst. You may be a barbarian, a monk, a knight, a wizard or merely a tourist. You may be human or not. At your side is a small animal companion, a dog or a cat.
I highly recommend that you check out the text version of the game at the NetHack Web site (see the on-line Resources), but make sure you visit Warren Cheung's SLASH'EM Web site, home of the “Super Lotsa Added Stuff Hack, Extended Magic” edition of NetHack. SLASH'EM is NetHack kept up to date with new levels, new monsters, spells and so on. Getting and building SLASH'EM is also easier than navigating through the various cryptic instructions for building the official NetHack. SLASH'EM provides a simple configure script making this an easy extract-and-build five-step:
tar -xzvf se008e0.tar.gz cd slashem-0.0.8E0 ./configure make su -c "make install"
To play, run the command slashem. You'll be asked whether you want the program to pick your character's race, role, gender and alignment for you or whether you'd like to choose all of these yourself. I usually prefer to make that choice myself, but you can get some interesting combinations by being brave and going totally random. Once this is done, a small introduction tells you about your character and which god you serve, gives you a nice pat on the back and sends you off to your doom. It's great fun.
With time, and in keeping with NetHack's evolution, graphical versions of the game came to be. By using graphic tiles and an easy-to-use menu-driven interface, the game took on a whole new dimension, all the while maintaining the same core functionality. One of these graphical incarnations is Mihael “miq” Vrbanec's gtk2hack (based on the SLASH'EM code), a great wrap-around of the latest version of NetHack that brings new life to the game (Figure 2).
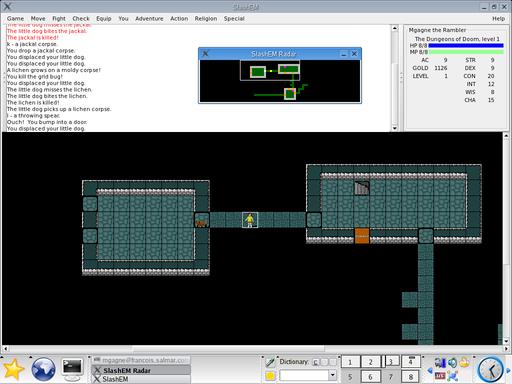
Figure 2. gtk2hack brings a clean graphical interface to NetHack along with a radar providing feedback on the explored areas.
As the name implies, gtk2hack is based on the GTK2 toolkit to provide the interface. It uses a two-dimensional overhead view with nice graphical tiles to display objects, monsters and so on. There's a small “radar” window that accompanies the main display that you can refer to during game play. Above the main graphical window, a game dialog is displayed along with the status of your possessions, your health, hit points, the level you are exploring and so on. If you have become familiar with text NetHack, you'll find this equally comfortable. Although you can navigate with mouse clicks, the same keystrokes apply.
Building gtk2hack is fairly straightforward—just another slightly modified extract-and-build five-step (skip the configure step). Because it comes with its own NetHack/SLASH'EM code bundled in, you don't need to download twice. Just remember that the executable is called gtkhack and not gtk2hack as you might logically expect.
One of the best graphical renditions of the game I have seen (and one of my favorite games) is Jaakko Peltonen's awesome Falcon's Eye. Although not as up to date as SLASH'EM in terms of story and development (it's based on NetHack 3.3.1, whereas SLASH'EM is based on 3.4.3), you have to try Falcon's Eye. It's that great, and if you still aren't hooked on NetHack, Falcon's Eye is sure to do the job. The dungeons enter the third dimension along with your character, your faithful companion dog and (of course) the monsters (Figure 3). The game is mouse-driven, and the graphics are high-resolution. There's a slick panel at the bottom of the screen from which you can access your possessions, your spells and other information. Like gtk2hack, there's also a small “radar” screen on the lower left so you can get a better view of where you are and where you have been.
Falcon's Eye is available as a source download, but I've found binaries for a number of distributions (Fedora, SUSE, Debian, Mandriva and others), so check your distribution CDs and your distro's contrib sites first.
Falcon's Eye starts in full-screen mode by default, which although cool, isn't what I want when I'm pretending to work while slaying goblins. To change the screen resolution to windowed mode, you need to edit the game's configuration file. It is called jtp_opts.txt, and you'll find it in the game's config directory. Here's the section you are looking for:
screen_xsize=800 screen_ysize=600 fullscreen=0
In the above example, I've already changed the resolution to windowed mode by setting fullscreen to 0. To return to full-screen mode, change it back to 1. Have a look at the file, and you'll find other interesting changes you might want to make. One is to make the walls transparent, or at least not quite as opaque. The reason you might want to do this is to make it easier to spot objects that might be against the walls as you navigate the dungeons. You can also decide whether you want music or sound effects to accompany your journey.
Speaking of journeys, exploring dungeons is extremely thirsty work, I'd rather avoid those strange potions as long as possible. Luckily, we have a rather generous wine cellar here at Chez Marcel. François, if you would be so kind....
The only catch with NetHack—okay, there are several catches—the biggest catch is that it may start to take over every bit of free time you have. Should you find yourself so addicted that you need to have NetHack with you wherever you go, consider downloading a copy of NetHack Linux. This is a single-floppy Linux distribution that boots up directly into a text-based game of NetHack. The most recent image contains NetHack version 3.4.3, the latest and greatest.
To get your copy of NetHack Linux, visit Benjamin Schieder's Web site (see Resources) and download the latest diskette image. Then, transfer the image to a diskette with the dd command:
dd if=nethacklinux_1.1.img of=/dev/fd0
To run NetHack Linux, simply pop the diskette in to any free PC's drive, reboot the system and a few seconds later, you are ready to go. A small menu appears from which you can edit the nethackrc file, show the current high scores or simply play the game. Select option one (Play NetHack), and you are ready to go.
I see by the clock on the wall that it is almost closing time. While François refills your glasses one final time this evening, let me direct you to a rather apropos, but strange little Web site. If, after crawling the Maze of Menaces for far too long, you start wondering what kind of NetHack monster you would be if you were a NetHack monster, I have just the Web site for you. Check out Kevan Davis' “Which NetHack Monster Are You?” site and answer the short questionnaire provided. The results can be entertaining or, in my case, embarrassing. Rather than embarrass myself by telling you, I'll merely point you to the on-line Resources for the address to the site. There's also the #nethack IRC channel on irc.freenode.net where dozens of people talk NetHack 24 hours a day. Finally, if you've had just enough wine (and if not, let François know) you may be ready for the NetHack theme song. Please raise your glasses, mes amis, and let us all drink to one another's health. A votre santé Bon appétit!
Resources for this article: /article/8531.