

Take a walk in your neighborhood and map the available wireless network connections with a free application.
We're clearly on the upside of the wireless wave, with new installations happening across the country and around the world every day. Like many technologies in an early emergent phase, providers still seem to be at a loss as to how to get the word out that they're making this valuable service available. Discovering the wireless networks in your community on your own can be a challenge. If you live in an urban area, it's likely that hundreds of publicly accessible wireless networks are just waiting for you to log in. If you live in a rural area, they may be harder to come by, but they're there. What you need is a set of tools to help you find and use the networks made publicly available for your convenience.
The first tool, of course, is the computer itself. Because of the near ubiquity, increasing power and decreasing size of laptops, they've become the tool of choice for wireless discovery. Or, you can go with the PDA. Though classified as a PDA (or, in the marketing parlance of Sharp, a Personal Mobile Tool) the power of the Zaurus makes it a de facto desktop in a pocket size. Armed with the proper software tools, the Zaurus is much lighter on the wrists and arms for discovering networks, while sacrificing virtually nothing in power.
The software tool of choice for discovering wireless networks with the Zaurus is Kismet, available as a .tar.gz file from killefiz.de/zaurus. Kismet can be used in tandem with Kismet-Qt, a clean and extremely friendly GUI interface that provides all the information you need to sniff and connect to the wireless networks in your community. You don't need a Zaurus to use Kismet; it works under any Linux system.
For a quick taste of the Kismet command-line interface, slide your wireless CF card into the CF slot and, from the terminal mode, enter kismet as root. Your network card will begin to flash rapidly, indicating that Kismet is sniffing for wireless networks by analyzing all packets it encounters.
The Kismet command-line application indicates the number of networks in close proximity, as well as the number of packets received and how many of those packets are encrypted. To configure the command-line tool to your particular preferences, use vi to edit /home/root/usr/etc/kismet.conf. This is a well-commented configuration file, providing detailed instructions for each configurable element of Kismet. There are many, all of which are applicable to your use of Kismet-Qt.
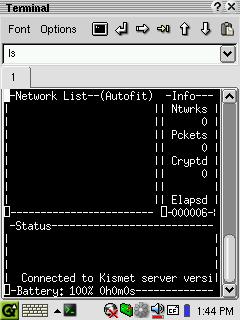
Figure 1. The Kismet Command-Line Interface
Installation of the Kismet-Qt application is a bit more straightforward. With the .ipk file downloaded and transferred to your Zaurus, the file appears in the Add/Remove Software option within the Tools tab. By default, the file actually is stored at /home/zaurus/Documents/Install_Files. You can select the application from the Add/Remove Software window, select install and your install location (internal Flash or an external storage device), then let the Zaurus do the heavy lifting for you. If you'd prefer to install the file using the terminal application, change to this directory and follow the ipkg instructions above to install.
Command-line Kismet installs a server from which the Kismet-Qt application pulls its information. If the Kismet server isn't running, Kismet-Qt throws an error noting it was unable to connect to this server. So, you need to start the server from the terminal window as above, then open the Kismet-Qt interface by selecting it from the applications button in the lower-left corner of your Zaurus screen. With the Kismet-Qt package installed and Kismet running in your terminal window, you're ready to start discovering open wireless networks. Let's take a look at the Kismet-Qt interface.
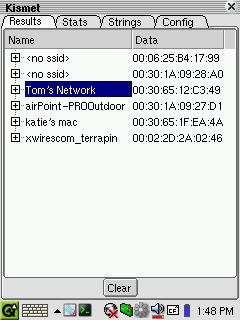
Figure 2. The Kismet-Qt Interface
As shown in Figure 2, the Kismet-Qt interface is broken out into four main tabs. These tabs display the current network activity, a statistical summary of all current activity, a summary of all special strings detected and a configuration screen. These tabs provide more than enough detail for most users to detect and connect to community wireless networks. Let's take a look at some of these tabs individually.
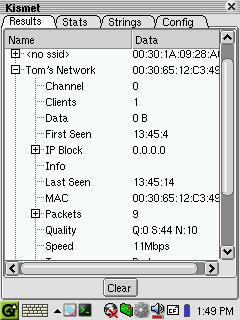
Figure 3. The Kismet-Qt Results Tab
Kismet-Qt retains the data on all network activity detected during the current session. This data is presented in the Results tab in collapsible form, identified at the top level by the network name (or ESSID). Although the Results tab provides a wealth of information, a caveat or two is in order when viewing discovered networks. In cases where the wireless network does not utilize an ESSID, the default name is displayed within angle brackets. Seeing a name within the list such as “linksys” may be an indication that you've stumbled upon a private wireless network operating in the manufacturer's default configuration. Although the owner's intention may be to provide this service to the community, tread lightly. If there's any question about the purpose of the network, avoid using the network you've detected.
The Results tab provides virtually all the information you need to establish a connection with an open wireless network. We'll discuss these items in a bit. In particular, you need to note the ESSID, whether the signal is WAP-encrypted, the IP-address range and the channel on which the network is operating. These are your keys to the wireless kingdom. You also may want to pay attention to the signal strength figures and the time the last activity was detected (“last seen”). This data will provide wireless users on the move with an indication of their relative location to the hot spot. A weaker signal indicates you're on the fringe of the hot spot, moving either in or out.
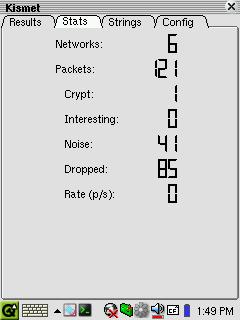
Figure 4. The Kismet-Qt Stats Tab
Kismet-Qt provides a clean interface to display the aggregate current wireless activity. This data includes the number of wireless networks currently within range, both the total number of packets received and the number that are encrypted, the signal noise level and the current packets-per-second receipt rate. Because this is an aggregate summary of the current activity, these numbers can be very high when encountering overlapping wireless zones. The rate-per-second figure, as with the signal strength and last seen figures above, can provide some indication of the user's movement into and out of the heart of a network.
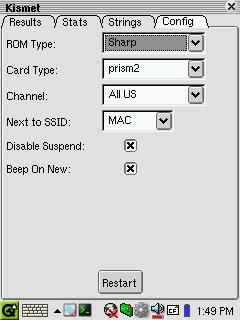
Figure 5. The Kismet-Qt Config Tab
The Config tab in Kismet-Qt contains the most critical data for making the Zaurus a wireless sniffer. You can select the system ROM type (Sharp or OpenZaurus) and the type of CF card you're using. Most common CF wireless cards are covered in the card type options, though you can modify the settings manually with the Other option if your card does not utilize one of the listed protocols. You also can select the operating channel from a list that provides the option of listening for specific individual channels or all US or international channels. The latter two options listen across the range of the US or international channels for any with current activity. Perhaps the most utilitarian option in the Config tab is the ability to beep when a new network is discovered.
The depth of the data provided by the Kismet/Kismet-Qt combination is quite rich. The tools provide all the data you need to sniff, connect to and utilize wireless networks in your community. Community wireless is coming to a town near you. With a Zaurus, Kismet and a wireless CF card, you can leverage the power of Linux to stay connected nearly anywhere.