

Ericsson Research is developing a new secure architecture for telecom applications on Linux clusters.
The interest in clustering from the telecommunications industry originates with the fact that clusters address carrier-class characteristics, such as guaranteed service availability, reliability and scaled performance, using cost-effective hardware and software. These carrier-class requirements now include advanced levels of security. There are few efforts, however, to build a coherent distributed framework to provide advanced security levels in clustered systems.
At Ericsson Research, our work targets soft real-time distributed applications running on large-scale Linux carrier-class clusters. These clusters must operate nonstop and must allow operators to upgrade hardware and software during operation, without disturbing the applications that run on them. In such clusters, communications between the nodes inside the cluster and to external computers are restricted.
In this article, we present the rationale behind developing a new secure architecture, the DSI (Distributed Security Infrastructure). DSI supports different security mechanisms to address the needs of telecom applications running on carrier-class Linux clusters. DSI provides these telecom applications with distributed mechanisms for access control, authentication, auditing and integrity of communications.
Many security solutions exist for clustered servers, but no solution is dedicated to clusters.
The most commonly used security approach is to package several existing solutions. Nevertheless, the integration and management of these different packages is complex and often results in the absence of interoperability between different security mechanisms. Additional difficulties also are raised when integrating many packages, issues like ease of system maintenance and upgrade, and difficulty keeping up with numerous security patches.
Carrier-class clusters have very tight restrictions on performance and response time, making the design of security solutions difficult. In fact, many security solutions cannot be used due to their high-resource consumption.
Currently implemented security mechanisms are based on user privileges and do not support authentication and authorization checks for interactions between two processes belonging to the same system on different processors. However, for telecom applications, only a few users run the same application for a long period without any interruption.
Applying the above concept will grant the same security privileges to all processes created on different nodes. This would lead to no security checks for many actions through the distributed system.
As part of a carrier-class Linux cluster, DSI must comply with the carrier-class requirements of reliability, scalability and high availability. Furthermore, DSI supports the following requirements: 1) Coherent framework: security must be coherent across different layers of heterogeneous hardware, applications, middleware, operating systems and networking technologies. All mechanisms must fit together to prevent any exploitable security gap in the system. 2) Process-level approach: DSI is based on a fine-grained basic entity, the process. 3) Minimal performance impact: the introduction of security features must not impose high-performance penalties. Performance can be expected to degrade slightly during the initial establishment of a security context; however, the impact on subsequent accesses must be negligible. 4) Preemptive security: changes in the security context will be reflected immediately on the running security services. Whenever the security context of a subject changes, the system will re-evaluate its current use of resources against this new security context. 5) Dynamic security policy: it must be possible to support runtime changes in the distributed security policy. Carrier-class server nodes must provide continuous and long-term availability; thus, it is impossible to interrupt the service to enforce a new security policy. 6) Transparent key management: cryptographic keys are generated in order to secure connections. This results in numerous keys that must be stored and managed securely.
DSI has two types of components: management and service. DSI management components define a thin layer that includes a security server, security managers and a security communication channel (Figure 1). The service components define a flexible layer that can be modified or updated by adding, replacing or removing services according to the needs.
The security server is the central point of management in DSI, the entry point for secure operation and management and intrusion detection systems. It also defines the dynamic security environment of the whole cluster by broadcasting changes in the distributed policy to all security managers.
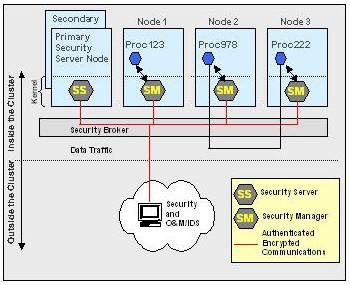
Figure 1. Distributed Architecture of DSI
Security managers enforce security at each node of the cluster. They are responsible for locally enforcing changes in the security environment. Security managers only exchange security information with the security server.
The secure communication channel provides encrypted and authenticated communications between security agents. All communications between the security server and the world outside of the cluster take place through the secure communication channel. Two nodes (to avoid a single point of failure) host the security server and different security service providers, such as the certification authority.
The security mechanisms are based on widely known, proved and tested algorithms. Users must not be able to bypass these mechanisms; therefore, the best place to enforce security is at the kernel level. All security decisions, when necessary, are implemented at the kernel level, the same as for the main security manager component, which has stubs into the kernel. These stubs are implemented through load modules.
The DSI architecture at each node is based on a set of loosely coupled services. Each service, upon its creation, sends a presence announcement to the local security manager, which registers these services and provides their access mechanisms to the internal modules. Two types of services, security services (access control, authentication, integration, auditing) and security service providers (for example, secure key management), run at user level and provide services to security managers.
So far, a secure boot mechanism for diskless Linux servers has been implemented. Using secure boot with digital signatures, a distributed trusted computing base (DTCB) will be available at the boot of the cluster nodes. The kernel at secure boot is small enough to be thoroughly tested for vulnerabilities. Furthermore, the use of digital signatures for binaries and a local certification authority will prevent malicious modifications to the DTCB.
We also implemented a security module based on the Linux Security Module (LSM), which enforces the security policy as part of the DSI access control service. This module is integrated with SCC to implement distributed access control mechanisms. DSI currently supports preemptive and dynamic security policy at the process level throughout the whole cluster.
To ease administration and maintenance of the distributed security policy, we are completing a study to devise methods of reusing information already contained in package management systems (such as RPM) in order to generate part of the security policy or to push such information to the package (if that is where it would be best specified). This effort also aims to use the policy to provide clearly different privileges during software installation, configuration, activation and execution. Specification of the exact language used to express the policy and of the compilation and loading mechanisms remain to be completed.
We have partly implemented a secure communication channel based on OmniORB, an open-source implementation of CORBA. SCC logics are implemented on top of a portability layer, making the implementation independent of any communication middleware used. The choice of CORBA as communication middleware for SCC was motivated by many factors, such as the support for distributed real-time and embedded systems and interoperability.
Our goal for DSI is to make the framework open source and to get people from different organizations and open-source initiatives involved in the design and development of the various components.
Figure 2 presents the various components of DSI. All components with a question mark are open to design and development contribution. Currently at Ericsson Research we are working toward implementing the core DSI, which includes the following: secure communication channel, security server, security manager, access control service (including LSM), security policy generation, security session manager and distributed tracing of events (as part of the auditing service).
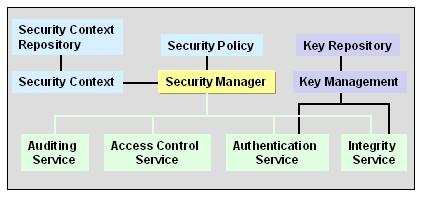
Figure 2. DSI Components
The DSI team from Ericsson Research will be available at the Ottawa Linux Symposium for three allocated presentations on DSI. We will also be available at the IEEE Cluster Conference 2002 in Chicago. In addition, Ericsson Research will be hosting the annual Open Cluster Group meetings June 24-25, in Montréal, which will give us the opportunity to address the members of the group and get them involved with the DSI Project.
A web site for the project is available as of June 2002. It provides DSI technical reports, presentations, source code and links to web sites of other contributors. Due to space limitations, we were not able to go into the details of DSI in this article. However, feel free to contact any of the DSI team members (listed below) to receive detailed papers on the DSI architecture, strategy and source code or to discuss collaboration opportunities.
Ibrahim F. Haddad (Ibrahim.Haddad@Ericsson.com), Charles Levert (Charles.Levert@Ericsson.ca), Makan Pourzandi (Makan.Pourzandi@Ericsson.ca) and Miroslaw Zakrzewski (Miroslaw.Zakrzewski@Ericsson.ca).
Marc Chatel (Marc.Chatel@lmc.Ericsson.se), Michel R. Dagenais (Michel.Dagenais@polymtl.ca), David Gordon (David.Gordon@Ericsson.ca), Bruno J. M. Hivert (Bruno.Hivert@Ericsson.com) and Dominic Pellerin (Dominic.Pellerin@Ericsson.ca).